
As a Certified Penetration Testing Engineer (CPTE), your role is crucial in ensuring the security and integrity of systems and networks. Penetration testing is a proactive approach to cybersecurity, aiming to identify vulnerabilities and weaknesses before malicious actors exploit them. In this ever-evolving digital landscape, where cyber threats continue to grow in sophistication, CPTEs need to equip themselves with a comprehensive set of penetration testing tools to effectively assess the security posture of organizations.
By leveraging the right tools, CPTEs can emulate real-world attacks, uncover hidden vulnerabilities, and provide valuable insights into the overall security of systems and networks. These penetration testing tools act as extensions of the CPTE’s knowledge and expertise, enabling them to simulate different attack scenarios and develop strategies to safeguard against potential breaches. With a strong understanding of these tools, CPTEs can effectively navigate the complexities of modern-day cybersecurity and assist organizations in fortifying their defenses.
Moreover, the role of a CPTE extends beyond the mere utilization of these tools. It requires a holistic understanding of networks, systems, and emerging technologies. CPTEs must possess a deep knowledge of different operating systems, network protocols, and programming languages to effectively assess the security posture of diverse environments. This comprehensive understanding allows CPTEs to adapt and tailor their testing methodologies, ensuring a thorough evaluation of an organization’s security controls. The following list highlights the top 10 penetration testing tools that every CPTE should know. These tools provide a foundation for identifying and fixing vulnerabilities, enabling you to conduct comprehensive penetration tests and secure your organization’s digital assets.

Nmap is a powerful penetration testing tool used for network exploration and security auditing. Nmap, which stands for “Network Mapper,” has the capability to discover hosts, services, and open ports on a network. It is particularly useful during the reconnaissance and penetration testing stages of security assessments. Certified Penetration Testing Engineers (CPTEs) can utilize Nmap to gain a better understanding of network architecture, identify possible entry points, and assess the overall security level of a system or network. By employing various scanning techniques, Nmap provides valuable insights that can enhance the security posture of a network.

Metasploit is a renowned penetration testing framework that simplifies the process of identifying and exploiting vulnerabilities. It provides a vast collection of exploit modules, payloads, and penetration testing tools. With Metasploit, CPTEs can simulate real-world attacks, validate system defenses, and effectively communicate risk to stakeholders.
The framework also facilitates the development of custom exploits, enabling tailored testing scenarios. The tool allows you to write custom test cases that help identify vulnerabilities. Further on, the findings are used to identify system-wide flaws and weaknesses.

Wireshark, a popular network protocol analyzer, is a must-have penetration testing tool for CPTEs. It allows you to capture and examine network traffic in real-time. By analyzing packets, protocols, and conversations, Wireshark aids in identifying suspicious activity, detecting network anomalies, and investigating security incidents. Its versatile filters and in-depth analysis capabilities make it an indispensable asset for network security assessments.
For best results, you can adapt the analyzer tool to work with discrete and confidential government agency security, commercial enterprise security, educational security, and other sector data.
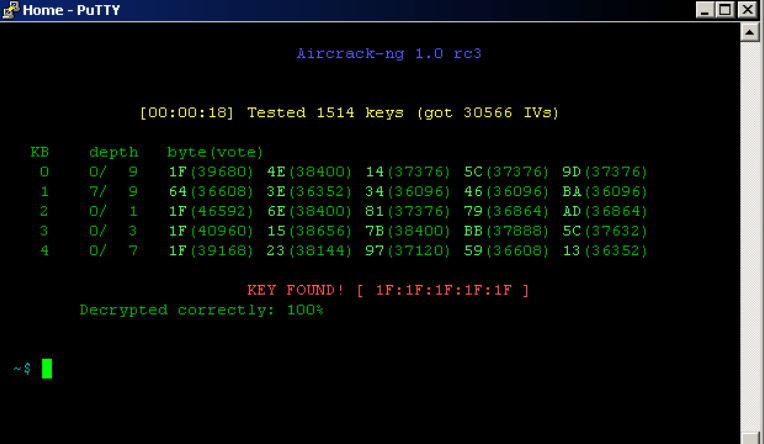
Wireless networks present unique challenges, and Aircrack-ng is a comprehensive suite of tools specifically designed for wireless security testing. CPTEs can leverage Aircrack-ng to assess the integrity of wireless networks by evaluating the strength of encryption protocols such as WEP and WPA. By identifying vulnerabilities and potential weak points, CPTEs can recommend mitigation strategies and enhance overall wireless network security.

Passwords remain a significant weak point in many systems, making password cracking a vital skill for CPTEs. John the Ripper is a renowned penetration testing tool that aids in identifying weak passwords and assessing the strength of password policies. By employing various techniques like dictionary attacks and brute-force methods, CPTEs can uncover passwords and strengthen system defenses against unauthorized access.
With John the Ripper, you will find wordlists supporting popular contemporary languages, password strength checking tools, modem password hashing tools, and much more.

The process of vulnerability scanning plays a crucial role in penetration testing, which aims to evaluate the security of systems and networks. One prominent tool widely used in this domain is Nessus. Nessus is a powerful vulnerability scanner designed to discover and highlight security weaknesses in various systems and networks. Using Nessus, Certified Penetration Testing Engineers (CPTEs) are able to conduct thorough scans that examine the target infrastructure. This scanning process helps identify a range of vulnerabilities, such as misconfigurations, outdated software versions, and potential entry points that could be exploited by malicious attackers.
The generated reports from Nessus are highly valuable as they provide a detailed overview of the identified vulnerabilities. These reports act as a roadmap for remediation efforts, offering guidance on the steps needed to address and mitigate the discovered security weaknesses. Armed with this information, organizations can prioritize and take appropriate actions to strengthen their security posture and protect against potential cyber threats

Burp Suite offers various features that aid in comprehensive web application security testing. One of its primary functionalities is the proxy, which acts as an intermediary between the user’s browser and the target application. This enables CPTEs to intercept and analyze the traffic between the two, thereby identifying potential vulnerabilities.
Additionally, Burp Suite includes a scanner feature that automatically scans the web application for known vulnerabilities. It leverages a database of security checks to detect common weaknesses like cross-site scripting (XSS) and SQL injection. By automating this process, CPTEs can save time and ensure thorough testing of the web application. This penetration testing tool allows CPTEs to automate attacks by providing various payload options and testing them against the web application. By systematically testing different inputs and payloads, potential vulnerabilities can be exposed and exploited, helping developers and security teams to address them effectively.

SQL injection refers to a type of attack where an attacker can manipulate a web application’s database by injecting malicious SQL code. To detect and exploit SQL injection flaws, a specialized tool called Sqlmap is used. Sqlmap automates the process of identifying and exploiting SQL injection vulnerabilities, allowing Certified Penetration Testing Engineers (CPTEs) to efficiently discover potential weaknesses in database-driven web applications. By understanding and utilizing Sqlmap effectively, CPTEs can uncover instances of data leakage and identify potential unauthorized access points within these applications.
Sqlmap will help you test across a broad spectrum of DBMSes, including MariaDB, MemSQL, MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, and several others.
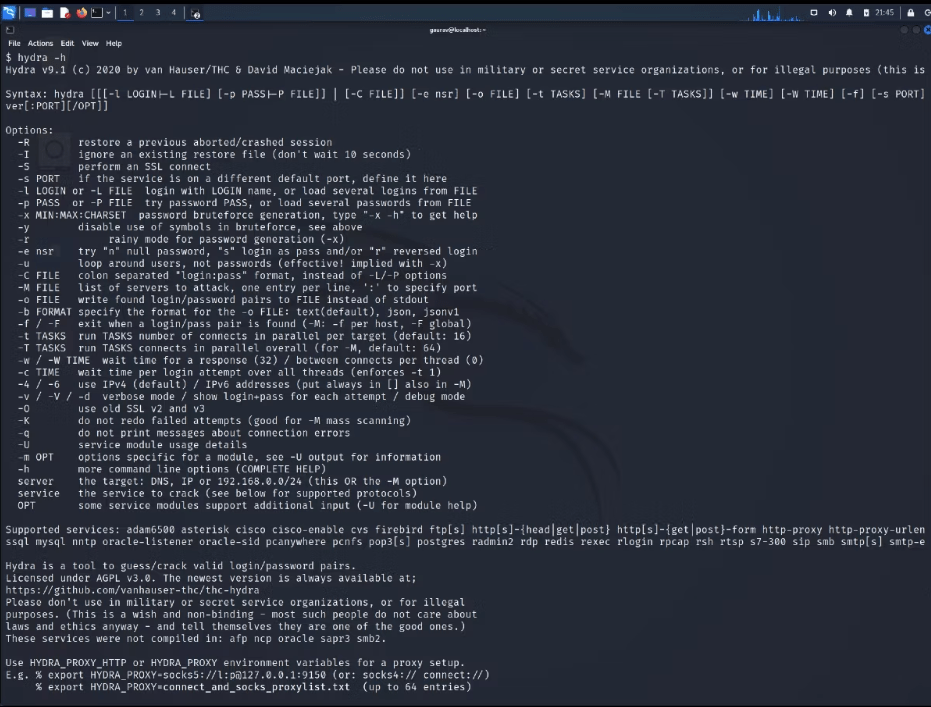
Hydra is a powerful tool used for cracking passwords and conducting automated brute-force attacks on different protocols such as SSH, FTP, Telnet, and HTTP. It systematically attempts various combinations of usernames and passwords to evaluate the effectiveness of authentication mechanisms and identify weak or easily guessable credentials. CPTEs utilize Hydra to assess the resilience of systems against determined attackers and provide recommendations for stronger authentication practices. Overall, Hydra enhances the capabilities of CPTEs in performing comprehensive security assessments.
The tool is highly versatile and has extended its support for new modules, including contemporary, less-known security/authentication protocols. This is handy for login protocol testing, commonly required for everything — from web portal security to application or system-wide security.

It is commonly used by Certified Penetration Testing Engineers due to its extensive capabilities. Netcat allows for the reading and writing of data across network connections, which is highly valuable for testing network security. Netcat’s functionality includes establishing connections, transferring files, and performing port scanning. This broad range of features makes it an essential tool for assessing network vulnerabilities and testing security measures. Additionally, Netcat can create backdoors or act as a listener, further enhancing its usefulness in penetration testing scenarios. Netcat is a powerful and flexible networking utility that CPTEs should be familiar with. Its ability to facilitate data transfer, establish connections, and scan ports, along with its capacity to create backdoors and act as a listener, make it an invaluable tool for testing network security and identifying potential vulnerabilities.
Mastering these top 10 penetration testing tools equips CPTEs with a robust foundation to effectively conduct penetration tests and identify vulnerabilities in systems and networks. However, it’s crucial to remember that the effectiveness of these tools heavily relies on the expertise and experience of the CPTE using them. Continuous learning, staying up-to-date with emerging threats, and expanding knowledge beyond these tools are essential to ensure comprehensive security assessments.
As a Certified Penetration Testing Engineer, your responsibility goes beyond the tools you possess. It includes a deep understanding of the underlying technologies, adherence to ethical guidelines, and effective communication of findings and recommendations. By harnessing the power of these tools, coupled with your expertise and analytical skills, you can contribute to enhancing the security posture of organizations and protecting digital assets from evolving cyber threats.
© Copyright Security Skool. All rights reserved| Designed By Clickedge Solutions Pvt. Ltd.
WhatsApp us